Tem Used to Describe an Attacker Watching a Potentioal Target
Cover for action explains why the person is doing what he or she is doing why that guy. A perpetrator first investigates the intended victim to gather necessary.
Its vital that the attacker tries to identify active machines on the target network.
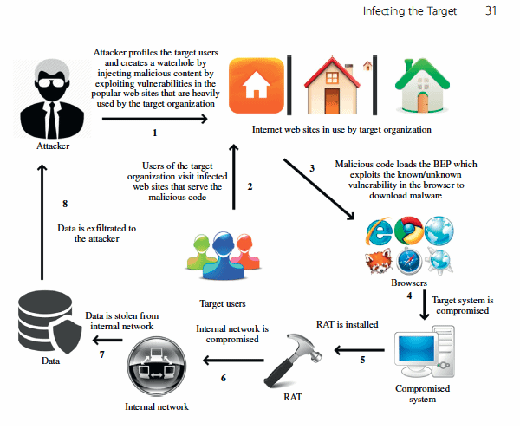
. Malware breaches a network through a vulnerability typically when a user clicks a dangerous link or email attachment that then installs risky software. A known target or victim machine. These are phishing pretexting baiting quid pro quo and tailgating.
As noted above surveillance is an integral part of the terrorist planning process for almost any type of attack although there are a. By directly interacting with a target the attacker can collect accurate and detailed information quickly but at the expense of potentially being identified as an attacker rather than just an innocent benign random visitor. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
While this is still an effective tactic attackers have added other methods to do this. Name and briefly describe three. Its vital that the attacker tries to identify active machines on the target network.
The Attackers Process. A type of threat in which threat actors actively pursue and compromise a target entitys infrastructure while maintaining anonymity. For the purposes of this article lets focus on the five most common attack types that social engineers use to target their victims.
A mobile device attack is an exploit targeting handheld communications devices such as smartphones and tablets. Threat Actor Hacker Attacker Whats the Difference. Attacker gathers information about the target using social engineering malware phishing OPSEC and automated vulnerability scanning.
When an attacker uses multiple techniques to compromise a target and such an attack is referred as. Because of their status if such an individual is successfully targeted he can be considered a big phish or alternatively a whale. These alternatives include watering hole attacks ie attacks that target websites frequently visited by the target industry or organization.
Facilitation extrinsic- Cyber attackers frequently use proxies and other systems to attack their final target. A person can pretend to be a student a businessman a repairman etc. Lets take a look at the common definitions for each of our personas.
Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. This can be represented by staring directly at or repeatedly glancing at the intended target. Social engineering attacks happen in one or more steps.
June an administrative assistant at the law. A potential threat that a hacker creates. Who are the experts.
Wants to get access to a prestigious law firm he has been watching for a while. Experts are tested by Chegg as specialists in their subject area. A method of attack to exploit a target.
The attacker will conduct initial research to identify basic background information about each potential target and identify questions that need to be answered prior to ultimately selecting a target. An attack in which the threat actor is almost always trying to make money as fast as possible and with minimal effort. We review their content and use your feedback to keep the quality high.
The terms used to describe these role-playing aspects of surveillance are cover for status and cover for action Cover for status is a persons purported identity his costume. According to Tech Target a threat actor also called a malicious actor is an entity that is partially or wholly responsible for a security incident that impacts or has the potential to impact an organizations security. Overview of Future Skills and Cyber Security A.
Attackers follow a fixed methodology. The steps a hacker follows can be broadly divided into six phases which include pre-attack and attack phases. State the process or methodology hackers use to attack networks.
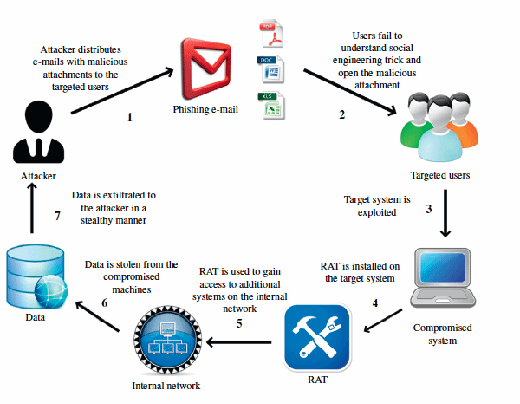
Social engineering is a term that encompasses a broad spectrum of malicious activity. Traditionally targeted attacks have used spear phishing emails to infiltrate the networks of targeted organizations. This research will be done through a variety of means but will most likely start off with online searches through various social media platforms.
For this reason it is important to note that some organizations and systems may simply be convenient targets which enable and facilitate attackers actions. Eyes on a Potential Target. One of the most obvious signs of potential trouble is paying repeated visual attention to an officers gun which could flag a gun grab but other targets of focus like the chin nose throat or eyes can be early warning signs of an attack.
In which phase of an attack does the attacker gather information about the target. Name and briefly describe three. The terms used to describe these role-playing aspects of surveillance are cover for status and cover for action Cover for status is a persons purported identity his costume.
When attack is done. Attackers use the information to identify possible attack vectors and create or. Social engineering or psychological manipulation.
A weakness that makes a target susceptible to an attack. A general term used to describe any individual who uses their technical knowledge to gain unauthorized access to an organization. Attacker identifies a potential target.
Active reconnaissance is the idea of collecting information about a target through interactive means. Cover for action explains why the person is doing what he or she is doing why. A vulnerability is not a threat but it is a weakness that makes the PC or the software a target for attacks.
During the reconnaissance probing and scanning stage that is engaged from an attack workstation the attacker can use the TCPIP family of protocols to conduct preliminary reconnaissance probing using Domain Name System DNS lookups and WHOIS to learn valuable information about an organization its IP addressing information and DNS names and their IP. Whale phishing is a term used to describe phishing attacks that are targeted specifically at wealthy powerful and prominent individuals such as C-level staff in corporates high ranking public officials and senior government ministers. Malware is a term used to describe malicious software including spyware ransomware viruses and worms.
To beat a hacker you have to think like one so its important to understand the methodology. What is the top method an attacker might infect a target. A person can pretend to be a student a businessman a repairman etc.

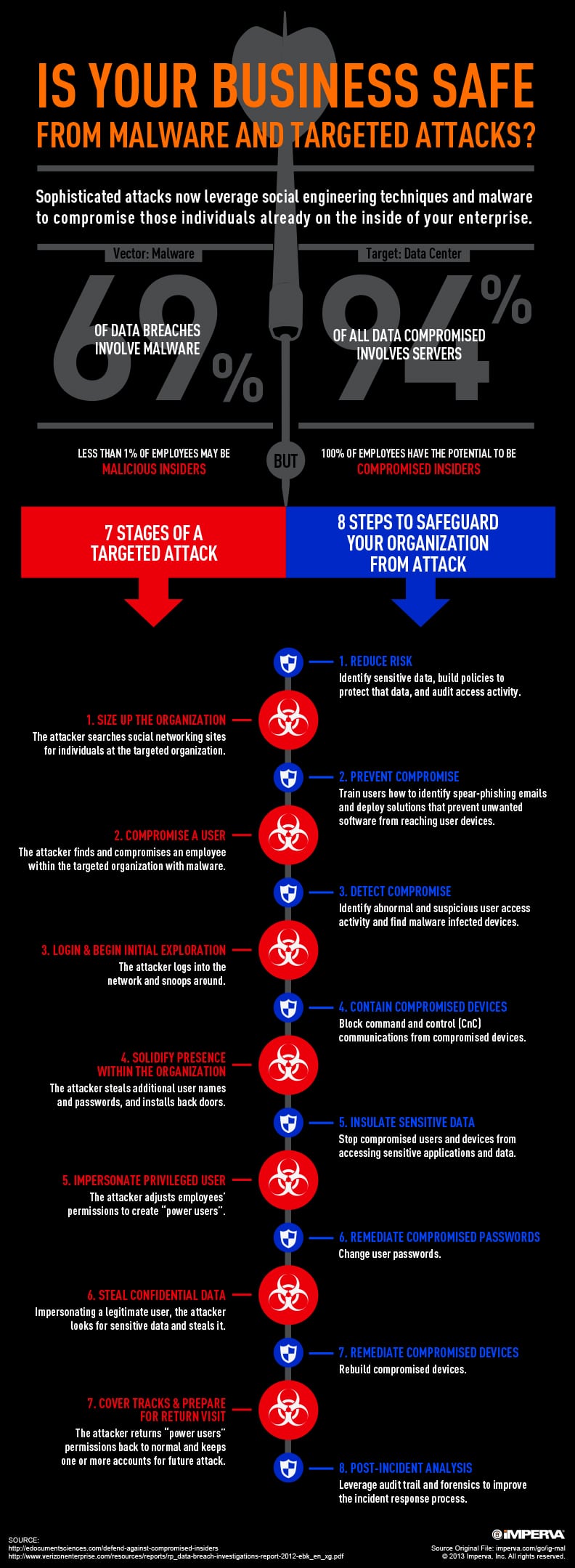
7 Stages Of An Advanced Targeted Attack Resource Library
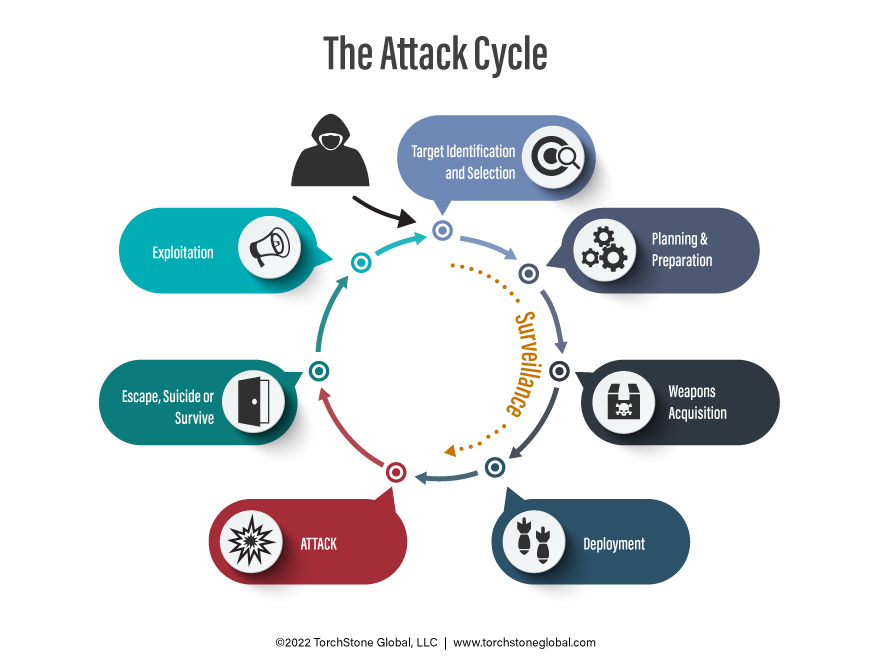
Exploiting Vulnerabilities In The Attack Cycle Torchstone Global
Comments
Post a Comment